Hackers Target Gamers With Microsoft-Signed Rootkit
Por um escritor misterioso
Last updated 19 setembro 2024

Kernel mode driver can download second-stage payload directly to memory, allowing threat actors to evade endpoint detection and response tools.
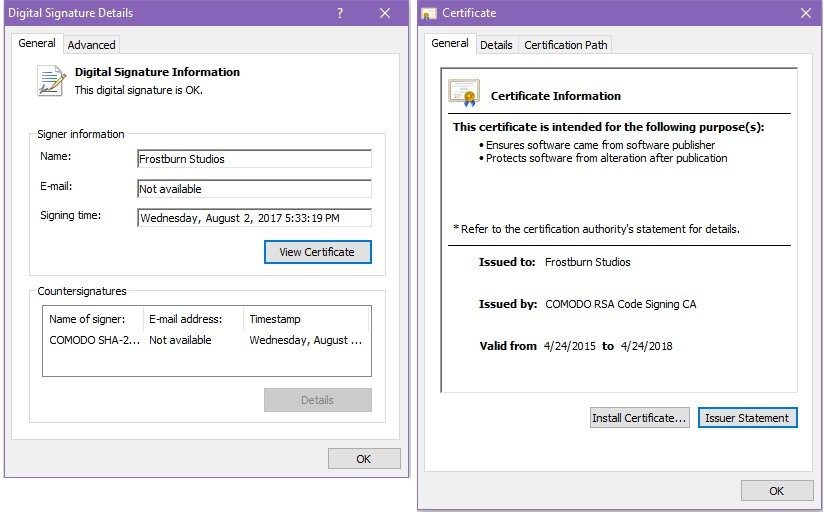
Chinese hacking group uses new 'Fire Chili' Windows rootkit

Hackers Trick Microsoft Into Signing Netfilter Driver Loaded With

What is a Rootkit & How To Deal With Them? - Littlefish

Microsoft Warns of New Russian State-Sponsored Hacker Group with

How to detect & prevent rootkits

Hackers Target Gamers With Microsoft-Signed Rootkit

Microsoft admits to signing rootkit malware in supply-chain fiasco

Hackers somehow got their rootkit a Microsoft-issued digital
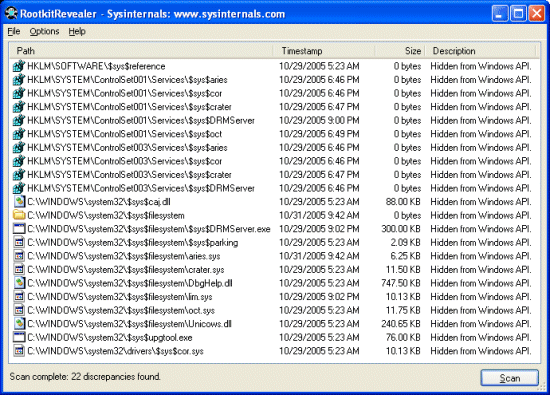
Sony, Rootkits and Digital Rights Management Gone Too Far

rootkit, Breaking Cybersecurity News

Netfilter Rootkit Malware Targets the Gaming Community: Microsoft
Chinese Hackers Utilize Microsoft Signed Rootkit To Target The

Microsoft accidentally signed a gaming driver containing rootkit
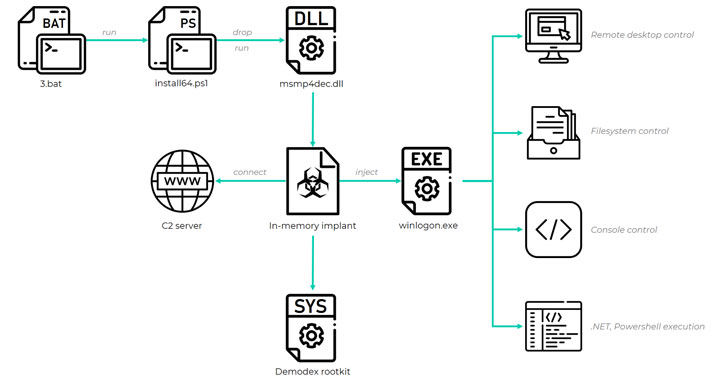
Chinese Hackers Used a New Rootkit to Spy on Targeted Windows 10 Users

Delivering vulnerable signed kernel drivers remains popular among
Recomendado para você
-
 Every day hacking, Roblox Creepypasta Wiki19 setembro 2024
Every day hacking, Roblox Creepypasta Wiki19 setembro 2024 -
Watch LankyBox Ultimate Mishmash Season 1, Episode 5: Roblox Challenge Tournament!19 setembro 2024
-
 hacker label #hackerroblox #roblox19 setembro 2024
hacker label #hackerroblox #roblox19 setembro 2024 -
 Helpful Hacking: Zoom Sponsors HackerOne's H1-702 Event19 setembro 2024
Helpful Hacking: Zoom Sponsors HackerOne's H1-702 Event19 setembro 2024 -
 Black Hat Hacker T-Shirt : Clothing, Shoes & Jewelry19 setembro 2024
Black Hat Hacker T-Shirt : Clothing, Shoes & Jewelry19 setembro 2024 -
 BT investigates Yahoo hack, tells BT Yahoo mail users to reset19 setembro 2024
BT investigates Yahoo hack, tells BT Yahoo mail users to reset19 setembro 2024 -
 Brazil's Digital Piracy Crackdown Grows, Eyes Metaverse19 setembro 2024
Brazil's Digital Piracy Crackdown Grows, Eyes Metaverse19 setembro 2024 -
Minecraft: Kaspersky reports growth in gamer cyberattacks in 202319 setembro 2024
-
 Leaked Roblox documents detail its quest for Chinese approval19 setembro 2024
Leaked Roblox documents detail its quest for Chinese approval19 setembro 2024 -
 Urban Decay Is Throwing the First Metaverse Makeup Launch Party on Roblox19 setembro 2024
Urban Decay Is Throwing the First Metaverse Makeup Launch Party on Roblox19 setembro 2024
você pode gostar
-
 League of Legends EU east Grandmaster - EpicNPC19 setembro 2024
League of Legends EU east Grandmaster - EpicNPC19 setembro 2024 -
 Hot Wheels Conjunto de pista de ação com 1 carro de brinquedo, 2 desaf19 setembro 2024
Hot Wheels Conjunto de pista de ação com 1 carro de brinquedo, 2 desaf19 setembro 2024 -
 Record of Grancrest War, Record of Grancrest War Wiki19 setembro 2024
Record of Grancrest War, Record of Grancrest War Wiki19 setembro 2024 -
 The Last of Us: Remastered wallpaper 03 1920x108019 setembro 2024
The Last of Us: Remastered wallpaper 03 1920x108019 setembro 2024 -
 Vtech Empurre e Gire o Pião : : Brinquedos e Jogos19 setembro 2024
Vtech Empurre e Gire o Pião : : Brinquedos e Jogos19 setembro 2024 -
 SPIDER-MAN Figure Miles Morales Spiderman 2 Marvel 15 cm19 setembro 2024
SPIDER-MAN Figure Miles Morales Spiderman 2 Marvel 15 cm19 setembro 2024 -
 Série turca disponível na HBO Max 5 séries turcas dubladas disponíveis na HBO Max19 setembro 2024
Série turca disponível na HBO Max 5 séries turcas dubladas disponíveis na HBO Max19 setembro 2024 -
 Caneca Flork- Acordada pela Força do Ó**o Mas c/ Paz - Rosa19 setembro 2024
Caneca Flork- Acordada pela Força do Ó**o Mas c/ Paz - Rosa19 setembro 2024 -
 Smother Meaning In Urdu, Baghola بگولا19 setembro 2024
Smother Meaning In Urdu, Baghola بگولا19 setembro 2024 -
Tata Steel hit by Dutch criminal probe - Frontline19 setembro 2024
