Cryptojacking - Cryptomining in the browser — ENISA
Por um escritor misterioso
Last updated 20 setembro 2024

The technique of hijacking browsers for mining cryptocurrency (without user consent) is called

Cryptojacking Miners for the first time on the Microsoft Store

PDF) Detecting Cryptojacking Web Threats: An Approach with
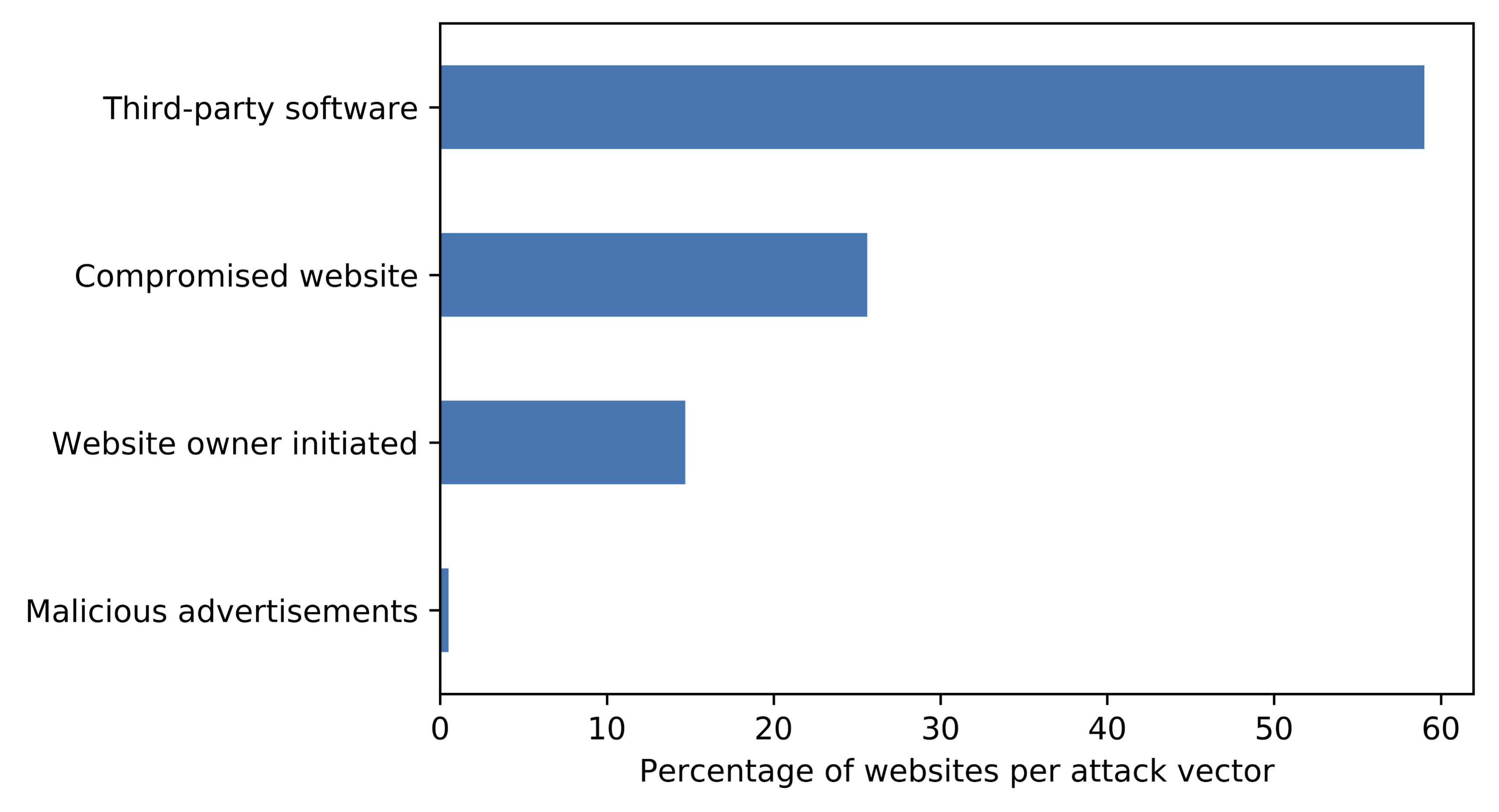
Blog: Infected third-party software key driver for cryptojacking

What is Cryptojacking? Detection and Preventions Techniques
Synthetic flow-based cryptomining attack generation through

Hundreds of new cyber security simulations to keep you safe from
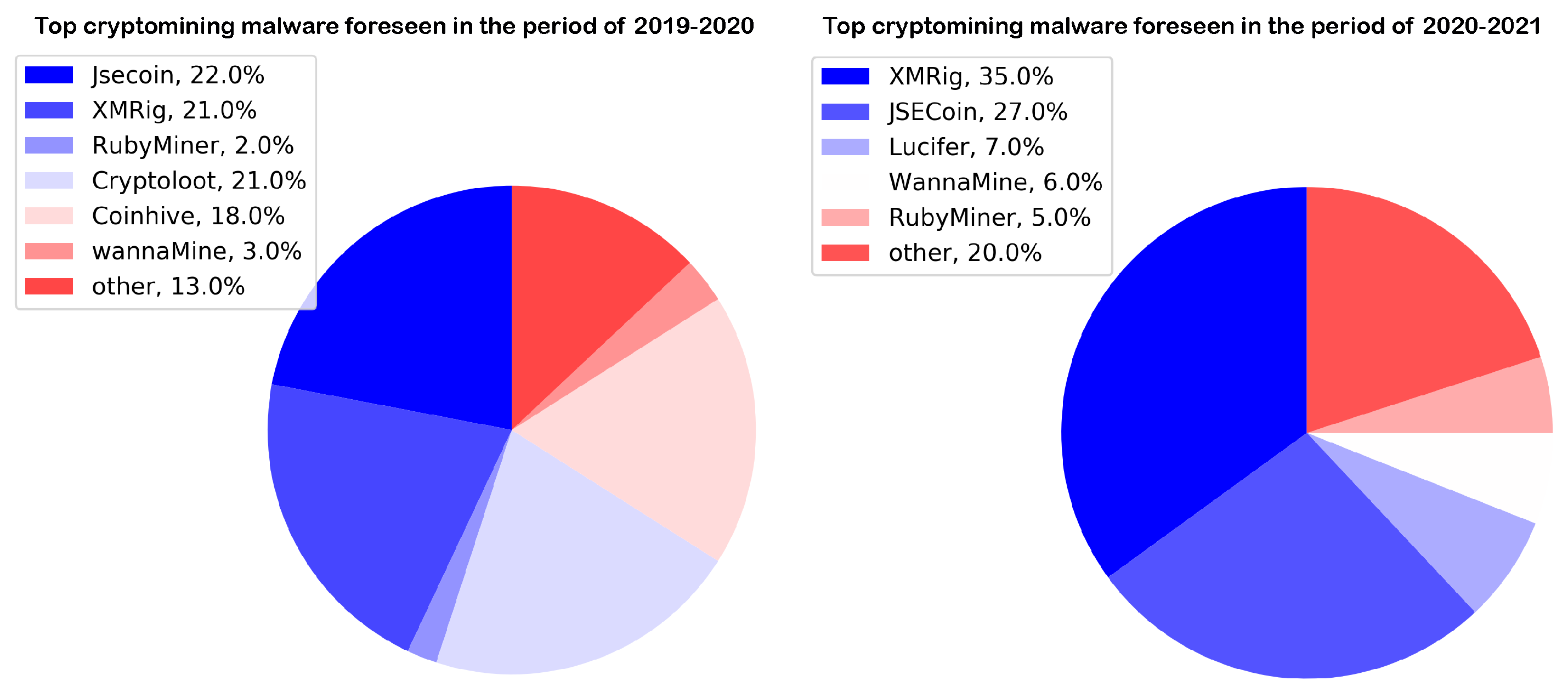
Applied Sciences, Free Full-Text
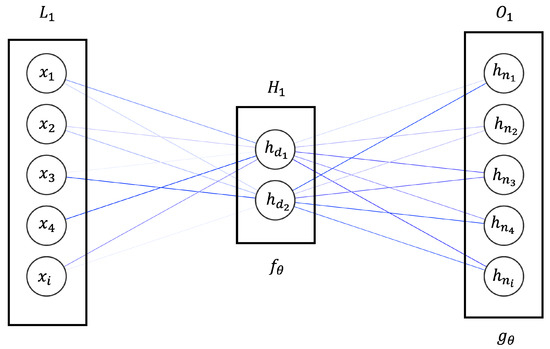
Applied Sciences, Free Full-Text

What is Cryptojacking? Detection and Preventions Techniques
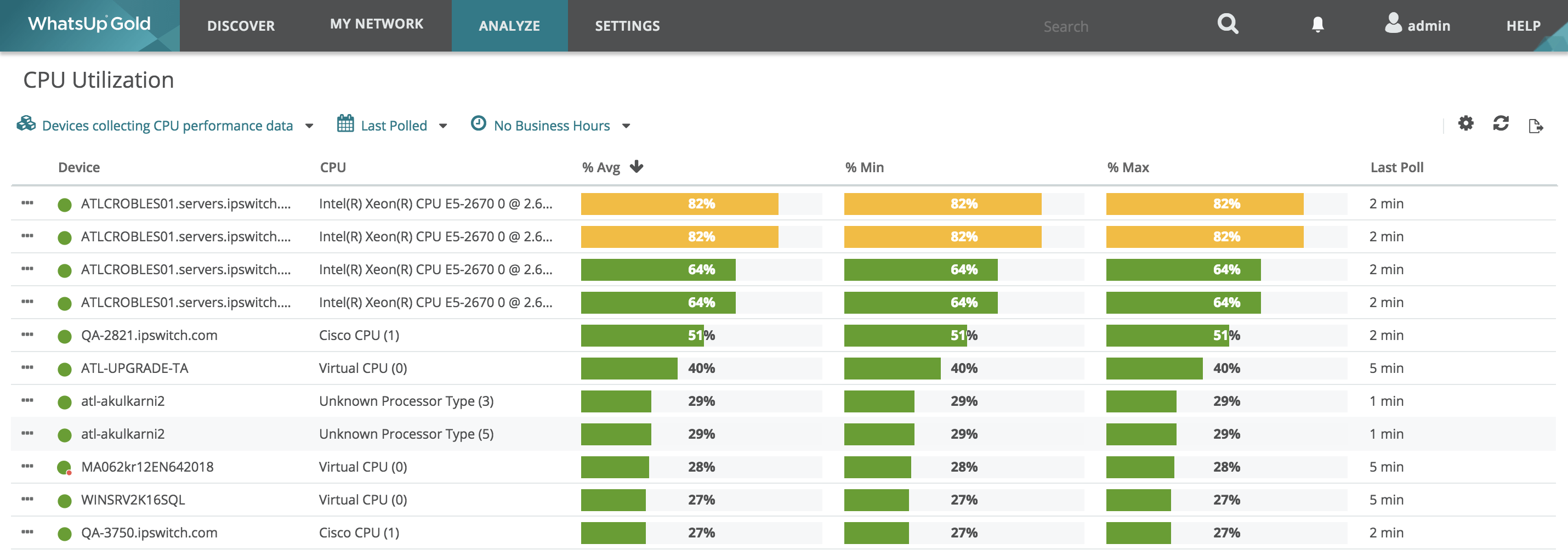
How to Detect and Stop Cryptomining on Your Network

What You Must Know About Cryptojacking in 2022
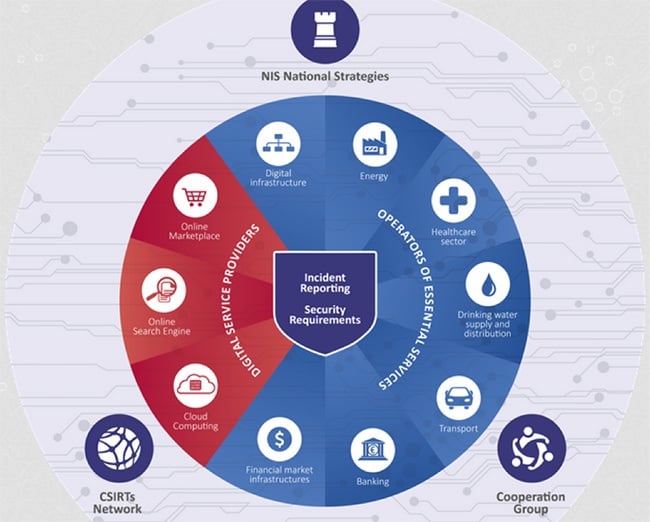
Which EU 2018 Directive Is More Important Than GDPR?
Recomendado para você
-
 Digmine Cryptocurrency Miner spreads via Facebook messenger20 setembro 2024
Digmine Cryptocurrency Miner spreads via Facebook messenger20 setembro 2024 -
 CryptoTab Browser- Overview. We earn cryptocurrency without investment, by Alex Rahmanin20 setembro 2024
CryptoTab Browser- Overview. We earn cryptocurrency without investment, by Alex Rahmanin20 setembro 2024 -
 Task Mining Desktop Application browser extensions (optional)20 setembro 2024
Task Mining Desktop Application browser extensions (optional)20 setembro 2024 -
 Cryptojacking Lets Strangers Mine Cryptocurrency With Your Browser20 setembro 2024
Cryptojacking Lets Strangers Mine Cryptocurrency With Your Browser20 setembro 2024 -
 21 Must-Have SEO Chrome Extensions to Follow in 202320 setembro 2024
21 Must-Have SEO Chrome Extensions to Follow in 202320 setembro 2024 -
 Testing your web browser for cryptojacking20 setembro 2024
Testing your web browser for cryptojacking20 setembro 2024 -
 Cryptojacking Extensions Found on Google Chrome Web Store20 setembro 2024
Cryptojacking Extensions Found on Google Chrome Web Store20 setembro 2024 -
 If You Value Your Privacy, Change These Browser Settings ASAP - CNET20 setembro 2024
If You Value Your Privacy, Change These Browser Settings ASAP - CNET20 setembro 2024 -
Introduction to Filter Lists – AdBlock20 setembro 2024
-
 Chrome Extension Hacked to Secretly Mine Cryptocurrency20 setembro 2024
Chrome Extension Hacked to Secretly Mine Cryptocurrency20 setembro 2024
você pode gostar
-
 Dragon Ball XENOVERSE 2 - Launch Trailer20 setembro 2024
Dragon Ball XENOVERSE 2 - Launch Trailer20 setembro 2024 -
 Switch Real Arcade Pro V Street Fighter (Ryu Edition) [ : : Games20 setembro 2024
Switch Real Arcade Pro V Street Fighter (Ryu Edition) [ : : Games20 setembro 2024 -
 The Last of Us Part 1” – Overpriced?20 setembro 2024
The Last of Us Part 1” – Overpriced?20 setembro 2024 -
toddynho em Promoção na Shopee Brasil 202320 setembro 2024
-
 DIY Painted Tic Tac Toe Rocks- Backyard Summer Camp20 setembro 2024
DIY Painted Tic Tac Toe Rocks- Backyard Summer Camp20 setembro 2024 -
 jogo do tigre qual baixar como jogar|Pesquisa do TikTok20 setembro 2024
jogo do tigre qual baixar como jogar|Pesquisa do TikTok20 setembro 2024 -
 Skip and loafer anime - BiliBili20 setembro 2024
Skip and loafer anime - BiliBili20 setembro 2024 -
 Elden Ring Winner 2022 Game Of The Year At The Game Awards Home20 setembro 2024
Elden Ring Winner 2022 Game Of The Year At The Game Awards Home20 setembro 2024 -
 HugeDomains.com Boots, Louis vuitton shoes, Fashion shoes20 setembro 2024
HugeDomains.com Boots, Louis vuitton shoes, Fashion shoes20 setembro 2024 -
 As melhores escolas de Orlando20 setembro 2024
As melhores escolas de Orlando20 setembro 2024
